Universal Trust Enforcement Platform
The Future of Security is Universal Trust Enforcement
Forge delivers a next–generation cybersecurity architecture that prevents identity compromise, blocks network intrusion, and replaces legacy VPN, SASE, and Zero Trust tools with real cryptographic protection.

70% of all breaches start with compromised credentials.
YouSource kills the attack chain before the credential is ever accepted.
Universal Trust Enforcement
Continous Trust. Continous Control.
Access is evaluated in real time. Every user, system, and AI agent is verified continuously. When trust changes, access changes immediately.
Only the Right People Get Access
Access isn’t granted once and forgotten. Every user, device, AI Agent and connection is checked continuously. If trust changes, access changes with it automatically.
There is no permanent access. There are no trusted networks. Nothing works unless it is allowed right now.
Why it matters: Stolen credentials and compromised accounts do not lead to full access or lateral movement.
Attacks Are Stopped Before Damage Happens
When something looks wrong, it is blocked immediately before files are encrypted, data is stolen, or systems are damaged.
Systems are intentionally separated. Networks, applications, data, and AI agents operate within enforced boundaries. A problem in one area cannot spread to another. No cleanup. No waiting. No guessing what happened later.
Why it matters: Threats are contained instantly and stopped before they can cause real damage.
Your Data Stays Protected Even During a Breach
Breaches happen. Exposure does not have to.
With YouSource, data is encrypted by default, access is temporary and tightly limited, and stolen access keys cannot be used.
Even if someone breaks in, they cannot do anything useful.
Why it matters: Ransomware, data theft, and token abuse fail by design.
Phishing and Social Engineering Stop Working
YouSource is built on the assumption that someone will eventually click, approve, or trust the wrong thing.
Access is adjusted continuously based on real behavior, and when trust changes, access narrows or collapses automatically. A single mistake cannot be used to move freely across systems or data.
Why it matters: Human error no longer turns into a company wide breach.
The Platform
Universal Trust Enforcement For Every Connection
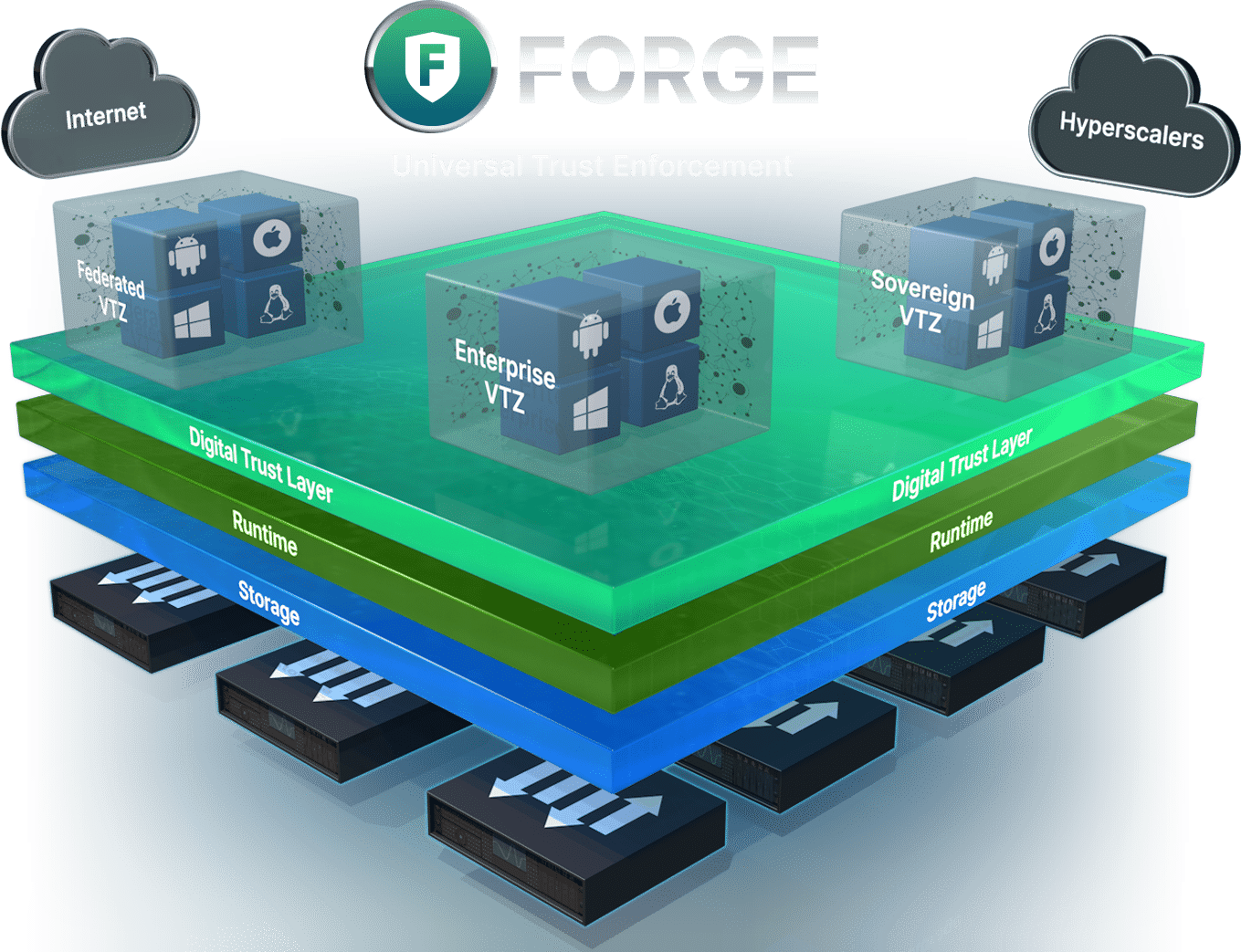
Universal Trust Enforcement (UTE) is the core security architecture developed by
YouSource. Forge merges identity and network security into a single trust layer.
Every packet is authenticated, every action is verifiable, and every connection is protected with cryptographic enforcement.
No replayable tokens
No lateral movement
No untrusted traffic
No legacy attack surface
The Platform
Universal Trust Enforcement For Every Connection
Forge merges identity and network security into a single trust layer.
Every packet is authenticated, every action is verifiable, and every connection is protected with cryptographic enforcement..
No Replayable Tokens
No Lateral Movement
No Untrusted Traffic
No Legacy Attack Surface

How It Works
AI Agent Trust Enforcement
AI agents act autonomously. They execute code, request access, move data, and make decisions without human involvement.
Universal Trust Threat Prevention ensures these actions are never trusted by default. Every action is evaluated as it happens, not assumed to be safe.
Each AI agent action flows through Forge’s Digital Trust Layer, where execution is evaluated in full context before proceeding. Actions that fall outside policy-defined trust are constrained or stopped immediately.
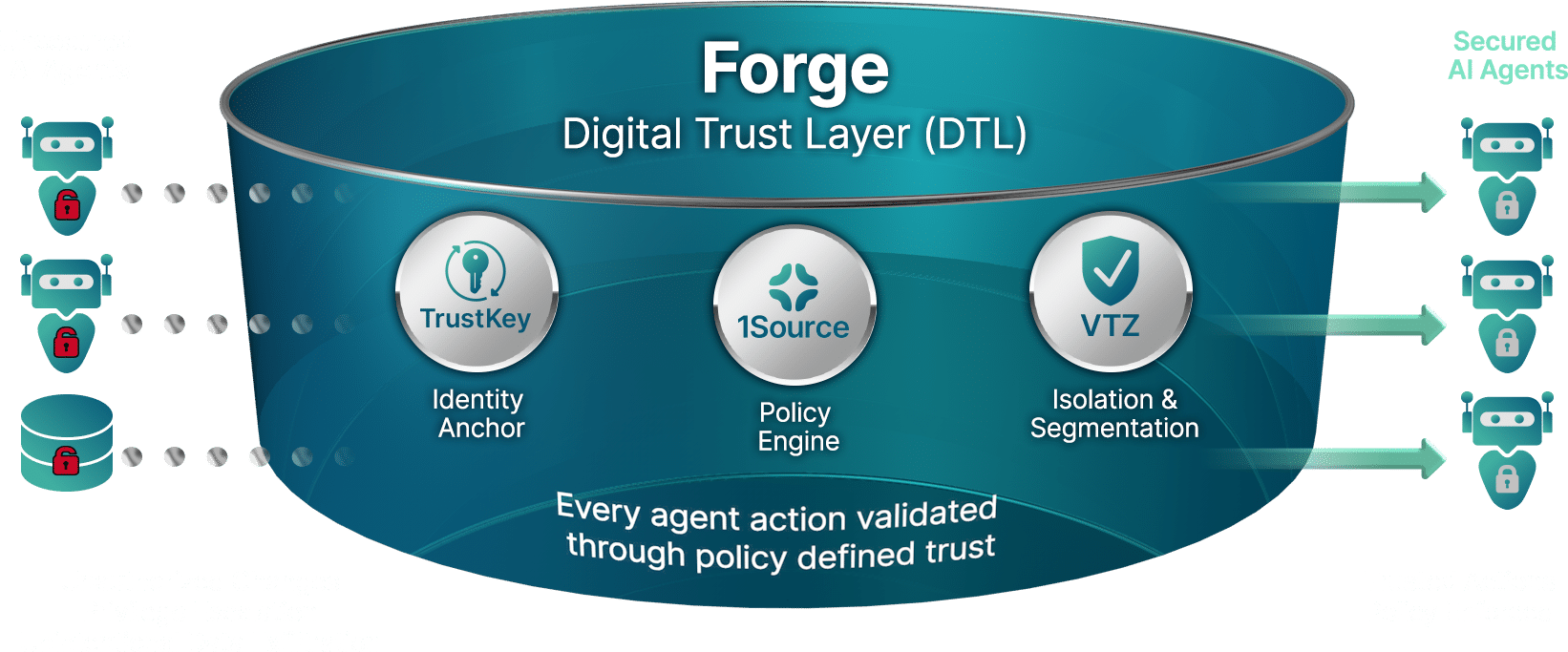
Forge evaluates AI actions in full context, not as isolated events. By understanding how access and behavior change over time, Forge enforces trust as actions occur, stopping risk early and allowing safe execution to continue.
The Breakthrough
What Makes Forge Different
Forge is not a VPN, a SASE product, or a Zero Trust proxy. It’s a foundational rewrite of how trust travels.
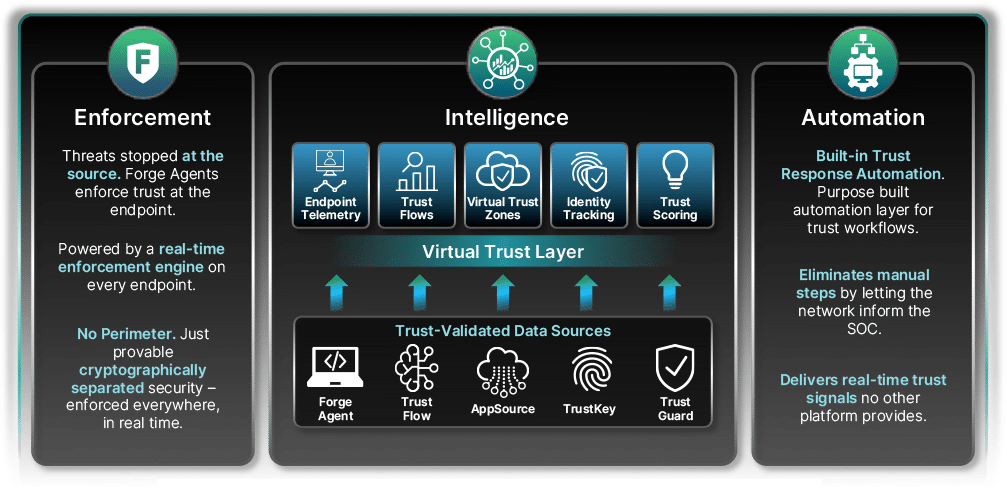
TrustOps – Universal Trust Automation & Intelligence
TrustOps provides automated trust enforcement, real-time prevention, AI-driven security analytics, and autonomous remediation.
It processes trust signals across every session and eliminates human wait-time, reducing attack dwell time to near zero.
TrustKey – Universal Trust Anchor
TrustKey is the hardware–backed cryptographic anchor of the Forge ecosystem.
It replaces passwords, tokens, SMS codes, authenticator apps, and all replayable credentials with a tamper–resistant identity bound to each device.
Forge – Universal Trust Threat Prevention
Forge is the world’s first Universal Trust Threat Prevention engine. It verifies every identity, authenticates every packet, and enforces trust before any connection is allowed.
Forge replaces VPNs, SASE, NGFW reliance, legacy token systems, and all tools dependent on reactive detection.
1Source – Universal Trust Identity & Policy Controller
1Source is the trust–native identity and policy controller for modern enterprise, replacing MFA, passwords, and brittle identity workflows with continuous, cryptographically anchored identity verification.
It’s the authoritative trust engine for devices, services, and users, enabling policy–driven access decisions across the entire network.
Why Universal Trust Enforcement Matters
Most cyber breaches originate from identity compromise or unrestricted network access.
Traditional security tools (NGFWs, EDR, XDR, ITDR, and SASE) were built on the assumption that breaches are inevitable. This forces companies into reactive detection and slow remediation.
Forge eliminates both root causes by embedding trust directly into the protocol. Threats cannot enter, move, or authenticate without verified cryptographic identity.
Success In Four Steps
Protect Your Users, Devices, Data, and AI
Identity is Proven
Every user, device, and app verifies its cryptographic identity through 1Source.
Trust Policy is Issued
1Source assigns a real-time policy based on who you are, what you’re doing, and where you’re going.
Traffic is Enforced by Agents
Devices run a lightweight Forge Agent that enforces trust inline, at the source, before data flows.
Real Time Verification
Trust-Flow telemetry feeds back into the AI engine, adapting policy continuously.
Insights From the Field
Cybersecurity Failure Patterns
Stay in the know by learning from YouSource about the causes of common cybersecurity failures.
